Public Key Infrastructure - CompTIA Security +
Hola,
I am preparing a entry about the Public Key Infrastructure referred to it as PKI. On a test as CompTIA Sec + this acronymous must be familiar as the names of your colleges. As they will fly over a conversation s asking "who is Peter?" (could be rude right?, especially when everyone knows Peter... great way to make friends... (・_・;)
Note: Stay tuned! I'll be creating related entries on these topics and will likely link them here, right?
In the past I found helpful IBM Technology Youtube Security Series. Jeff Crume one of their engineers is the teacher I always wish I had. To understand where I'm going look at this video about the PKI.
Then I will recommend you to look where the magic is with this example about asymmetric keys, that I found very cool (except the maths at the end... (¬_¬”) ey but is ok! I'm not perfect.Diffie-Hellman Key Exchange
That is fine but... while the overview is okay, I know there's a much deeper image to explore.
To truly grasp this whole thing, I needed to create a more comprehensive understanding. And about Peter... (Who is Peter?... Just kidding, it doesn't matter. No, wait, it really doesn't. (ʘ‿ʘ)
This time, the following content was developed with the assistance of AI. Let me walk you through the process so you can read on with some peace of mind (that's how I'd want to be treated reading a random blog online), so...
I used the study guide from Dion's CompTIA Security+ course on Coursera as my primary knowledge source.
While helpful, I need a more interconnected and detailed "big picture"—you name it! I rely on an AI study tool called NotebookLM (yes, it's Google, but trust me, it's "ok" for learning with the right references). Visualisations with Napking.
However, I found my own notes lacking depth, so I consulted AI language models (Gemini -.- and Grok ༼ ʘ‿ʘ༽) to arrive at this final study note i want to share to the world.

What is PKI?
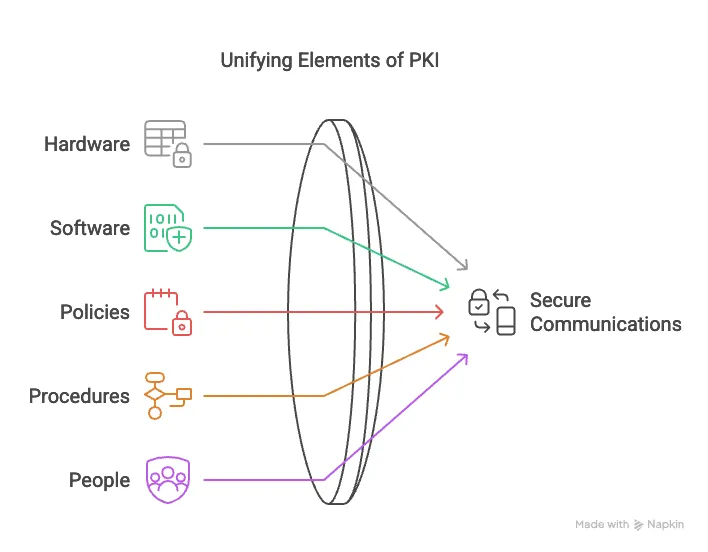
- A framework and system for managing digital certificates and cryptographic keys.
- Involves hardware, software, policies, procedures, and people to enable secure communications.
- Primarily uses asymmetric cryptography (public and private key pairs), but also supports hybrid cryptography.
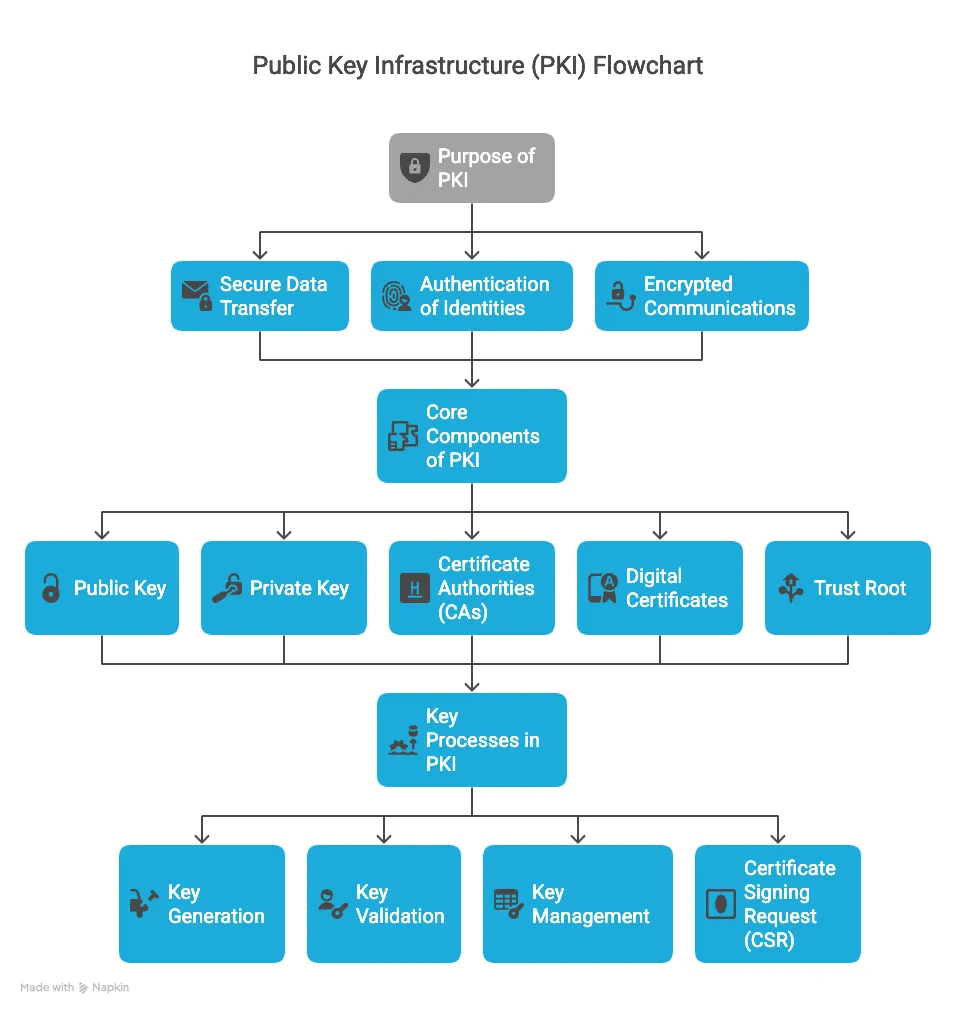
Purpose of PKI
- Manages keys and digital certificates to ensure:
- Secure data transfer.
- Authentication of identities.
- Encrypted communications (e.g., HTTPS, VPNs).
- Provides security, reliability, and trust in digital interactions.
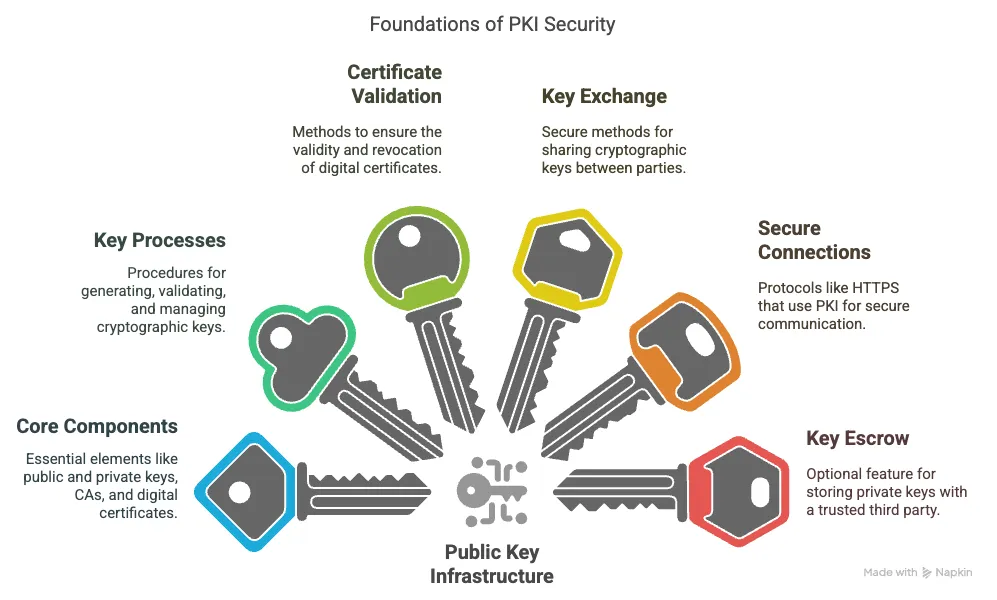
Core Components of PKI
- Public Key: Encrypts data or verifies signatures.
- Private Key: Decrypts data or creates signatures.
- Certificate Authorities (CAs): Trusted entities that issue and manage digital certificates.
- Digital Certificates: Bind public keys to identities for authenticity.
- Trust Root: Foundational CA certificates establishing trust in the PKI hierarchy.
Key Processes in PKI
- Key Generation: Creates public-private key pairs.
- Key Validation: Verifies the legitimacy of keys and their issuance.
- Key Management: Oversees the lifecycle of keys (distribution, rotation, revocation, destruction).
- Certificate Signing Request (CSR): A request to a CA for a digital certificate.
Key Exchange in Cryptography
- A method to securely share cryptographic keys between parties.
- Uses asymmetric algorithms like Diffie-Hellman (Vulnerable to man-in-the-middle (MITM) attacks without authentication (e.g., digital signatures or certificates) or RSA.
- Often part of hybrid encryption, where a symmetric session key is exchanged for faster communication.
PKI in Secure Connections
- Used in protocols like HTTPS (TLS/SSL) to:
- Authenticate servers (and optionally clients).
- Establish secure connections via key exchange.
- Generates a random session key using asymmetric cryptography for symmetric encryption during the session.
Certificate Validation and Revocation
- Certificate Revocation Lists (CRLs): Lists certificates that are no longer valid.
- Online Certificate Status Protocol (OCSP): Provides real-time certificate status checks.
Key Escrow in PKI
- An optional feature where private keys are stored by a trusted third party.
- Enables key recovery for lost keys or legal purposes.
- Raises security and privacy concerns, requiring strict controls; not always implemented.