Tools of the trade - IBM Cybersecurity Architecture Series
Hola!
During my CompTIA Security+ preparation, I found this to be a great source of depth, compared to other guides or courses I’ve mentioned here so far. I’m going to write the notes I took during these videos using 0s and 1s. Hope it helps you too!
Common IT Architecture Diagrams.
These are the "lingua franca" or common language of IT architects. A cybersecurity architect needs to understand how a system works using these diagrams.
Business Context Diagram: Shows the relationships between different entities or stakeholders in a system at a high level, often from a business line perspective.
System Context Diagram: Breaks down the business context to show what it would look like in an IT system, including the system’s main components.
Architecture Overview Diagram: Dives into a greater level of detail than the system context diagram, showing more specific components and their interrelationships.
Tools of the Trade:
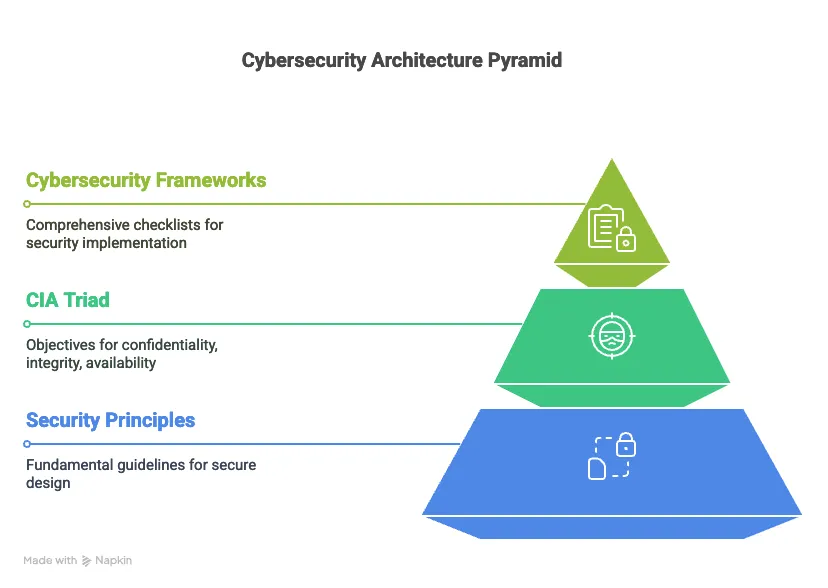
Security Principles: The architect applies fundamental principles like Defense in Depth, Least Privilege, Separation of Duties, Security by Design (also known as "Shift Left," moving security to the early stages of the project lifecycle), and K.I.S.S. (Keep It Simple, Stupid). Security by obscurity is the principle to avoid. Applying these principles is key to ensuring a secure architecture.
The CIA Triad: Confidentiality, Integrity, and Availability are presented as a checklist to determine if a cybersecurity architecture has been done correctly. Everything done in security aims to achieve one or more of these objectives.
Cybersecurity Frameworks: The architect uses frameworks like the NIST Cybersecurity Framework in the United States. This framework serves as a comprehensive and detailed checklist with the following functions or stages:
Subscribe to my blog
