DLL Injections and System API Notes
Hola!
Today studying about DLL injections, I found that many times on blogs, the vocabulary and definitions are this lovely mix of different levels of concretion when speaking about technical terms — depending, let's say, on the author's taste. (Which is just a quick impression, and why not, it's funny imagining us as chefs adding spaces creatively to our blog posts depending on our taste.)
All started after I noticed there was more detail I wanted to draw in this page.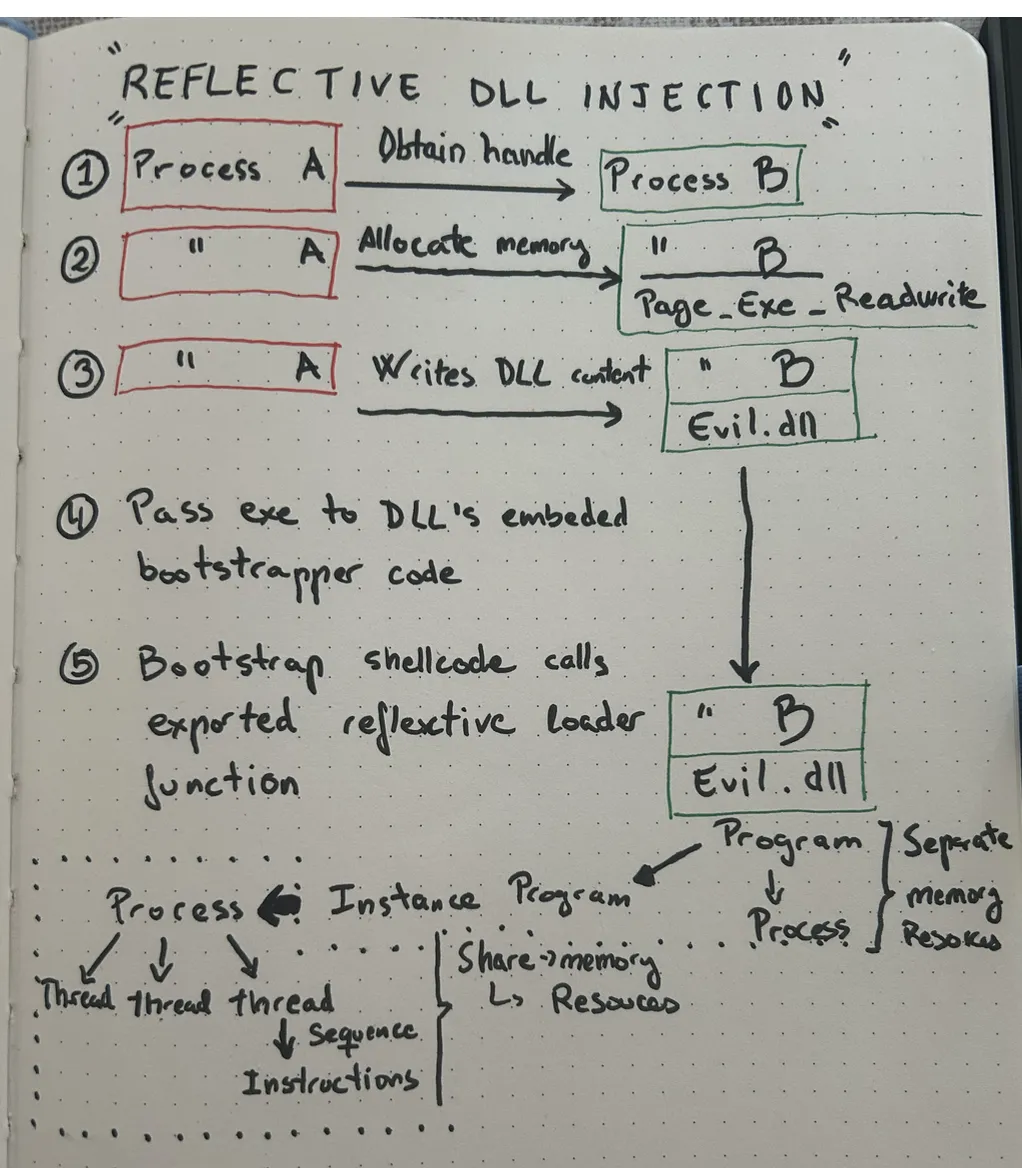
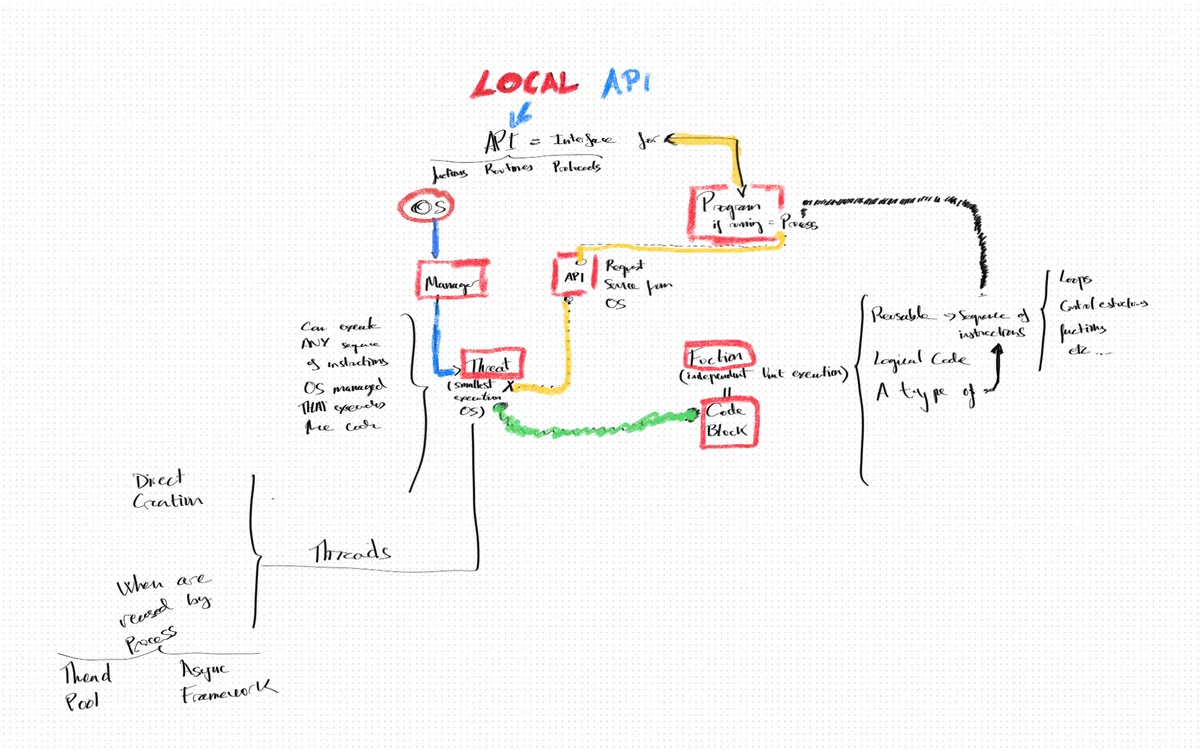
Code Execution Hierarchy in an OS
I have this hierarchic execution of code on an OS:
- OS → Manages the processes (programs at execution)
- Processes → Can have one or more threads
- Threads → Execute functions / code blocks (sequences of instructions)
- Functions / code blocks → Can contain different types of instruction sequences like loops, control structures, other functions, etc.
My Questions While Reading
During my reading I asked myself:
- In real terms, what is the difference between a process and a thread?
- What is the function of an API on a Windows OS?
All this just to understand the bigger picture behind injections and their types.
I noted that an API can validate data and also carry out system calls.
When I first encountered the term "Thread Manager", I realized in this context it referred to the thread scheduling program in the OS.
Also, system APIs may not validate data, which I misunderstood based on my readings on remote API semantics.
Another reflection: I need to be cautious not to confuse protocol with interface in my reasoning.
Here, protocol refers to communication rules like HTTP, not input validation logic.
Commonly Targeted Windows APIs for Attacks
Here are some commonly abused APIs attackers use in the context of injections and persistence:
Process and Thread Manipulation
- APIs:
CreateProcess,OpenProcess,CreateRemoteThread - Use: Process injection, privilege escalation, persistence
DLL Injection
- APIs:
LoadLibrary,WriteProcessMemory - Use: Injecting malicious code into another process
File and Registry Access
- APIs:
CreateFile,ReadFile,WriteFile, registry functions - Use: Modify files or registry keys for configuration/persistence
Network Communication
- APIs:
WSAStartup,socket,connect - Use: Enables backdoors, C2 channels, data exfiltration
Windows Credential APIs
- Examples: LSA and Credential Manager
- Use: Extract or abuse stored credentials
Windows Management Instrumentation (WMI)
- Supports:
- Persistence: via scripts, scheduled tasks
- Reconnaissance: Gathering system/network info
Service Control Manager (SCM) API
- APIs:
OpenSCManager,CreateService,StartService - Use: Install or run malicious services
COM and OLE APIs
- Use: Automation and inter-process communication
- Abuse: Office macros, automation-based attacks
Network Protocol APIs
- Protocols: SMB, RPC, HTTP
- Use: Lateral movement, RCE, exfiltration
Extra Note on Threads and Async
I found there's an important differentiation in thread creation models that I wasn’t aware of:
- Threads can be created directly.
- They can also be reused via mechanisms like thread pools or async frameworks.
Discuss this post: Bluesky
Bibliography
Maloney, David "thelightcosine". "Weaponizing the Windows API." DEFCON 20, 2013.
[YouTube Video, Timestamp ~22:20–28:00]
Discusses how attackers leverage Windows APIs (such as credential store and cryptographic APIs) for post-exploitation, including credential extraction and system manipulation.
Source: https://www.youtube.com/watch?v=cZ-evXHTWIQWeissman, Jonathan S., & Meyers, Mike. CompTIA Network+ Certification Passport (Exam N10-008). McGraw Hill, 2022.
[See: Application Layer, APIs, and Protocols, pp. 78–82, 85–98]
Explains the OSI model, the role of APIs at the Application layer, and how protocols and APIs interact in networking and security contexts, including how attackers may target these interfaces.Meyers, Mike, & Soper, Mark Edward. CompTIA A+ Core 2 Certification Passport (Exam 220-1102). McGraw Hill, 2023.
[See: Windows OS Security Features, Application Security, and OS Components, pp. 1–6, 15–20, 60–70]
Details Windows OS architecture, built-in APIs, and how applications interact with the OS, including security implications and common attack surfaces.