Cybersecurity Principles: IBM Cybersecurity Architecture Series
Hola!
I decided to go over my notes today, this is a note on IBM Cybersecurity Architecture Series to support general concepts mental map. I love the video series! I 100% recommend to watch them.
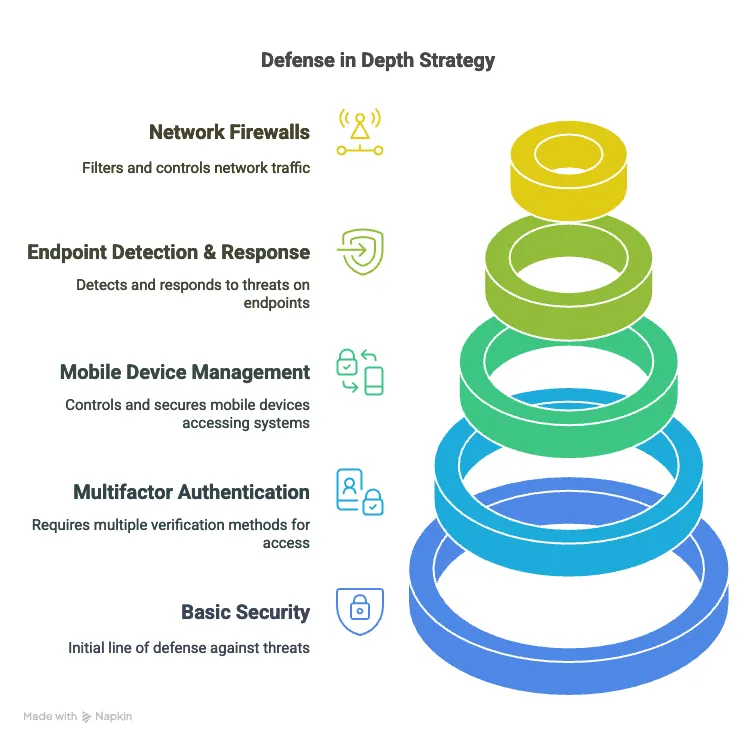
 Defense in Depth Principle: This principle aims to create an obstacle course for attackers, not relying on a single security mechanism to keep the system secure. The idea is that if one mechanism fails, the rest of the system continues to function. It’s illustrated with the example of a castle with walls, a moat, and a drawbridge, and in modern security with the application of multiple layers like multifactor authentication (MFA), mobile device management (MDM) software, endpoint detection and response (EDR) capabilities, and network firewalls. It seeks to avoid single points of failure and achieve a system that, if it fails, does so safely (fail-safe).
Defense in Depth Principle: This principle aims to create an obstacle course for attackers, not relying on a single security mechanism to keep the system secure. The idea is that if one mechanism fails, the rest of the system continues to function. It’s illustrated with the example of a castle with walls, a moat, and a drawbridge, and in modern security with the application of multiple layers like multifactor authentication (MFA), mobile device management (MDM) software, endpoint detection and response (EDR) capabilities, and network firewalls. It seeks to avoid single points of failure and achieve a system that, if it fails, does so safely (fail-safe).
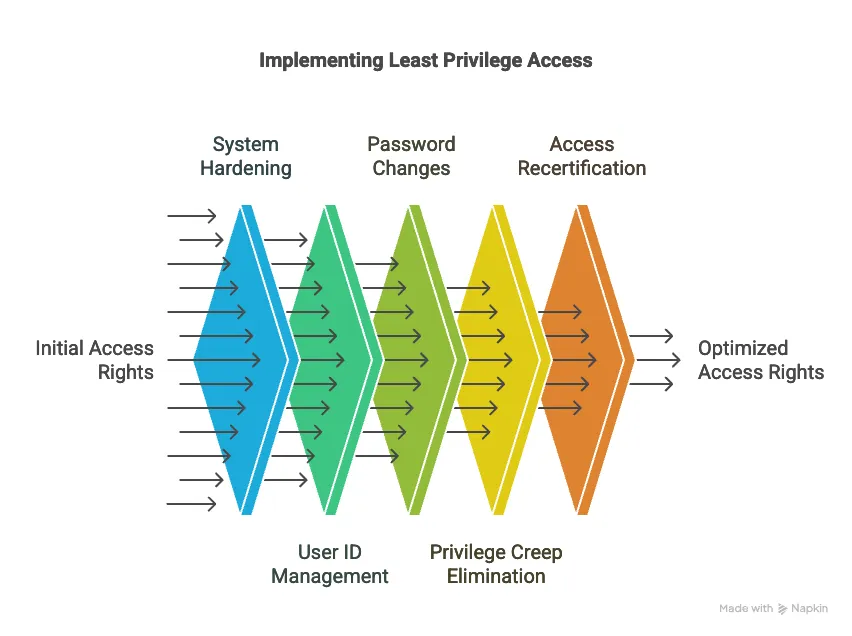
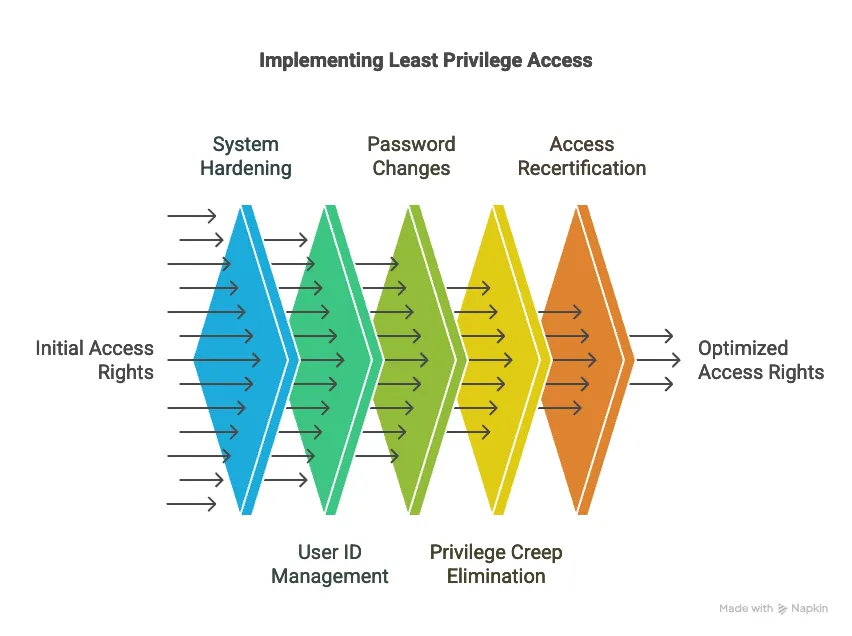
Principle of Least Privilege: This principle states that access rights should only be granted to individuals who need them to perform their job, justifiably, and only for the time they need that access. It involves system hardening, which may include removing unnecessary services (like FTP or SSH on a web server if not used), deleting unnecessary user IDs, and changing default usernames and passwords. It also addresses eliminating "privilege creep", which occurs when users accumulate access rights "just in case," and suggests conducting annual (or more frequent) recertification campaigns to review users’ access rights and remove them if no longer needed.
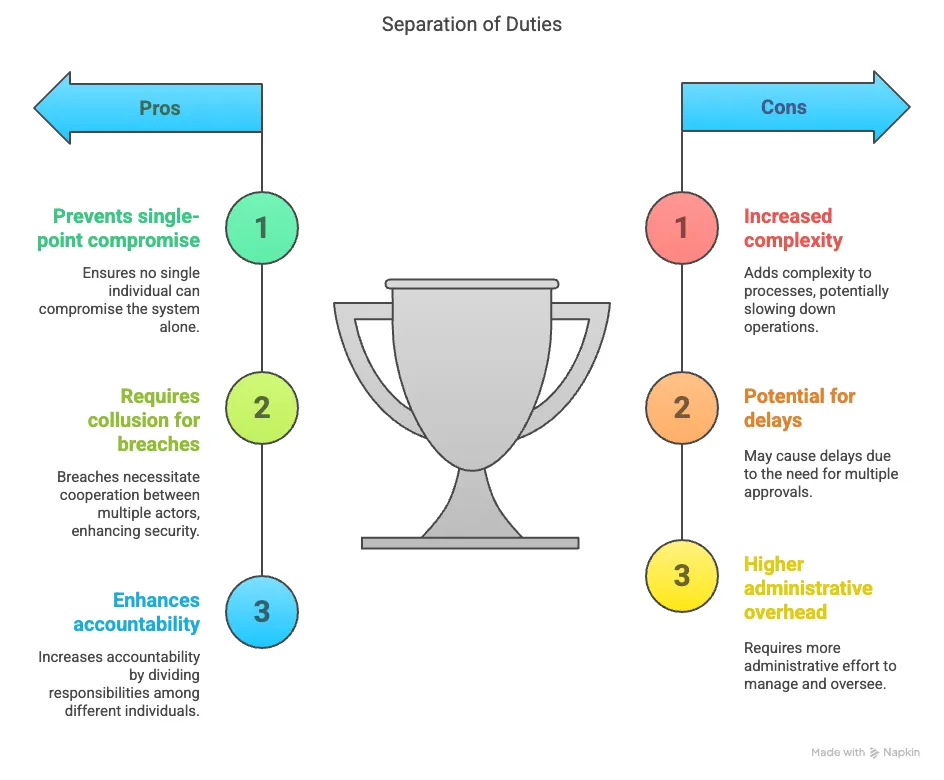
- Separation of Duties Principle: The idea is to avoid any single point of control. It seeks to force collusion (the cooperation of two or more actors, often "malicious") to compromise the system. No single person should be able to create a compromise on their own. A physical example is a door with two locks requiring different keys held by different people. In an IT case, it means the person requesting something (like access to a database or a funds transfer) should not be the same person approving it.
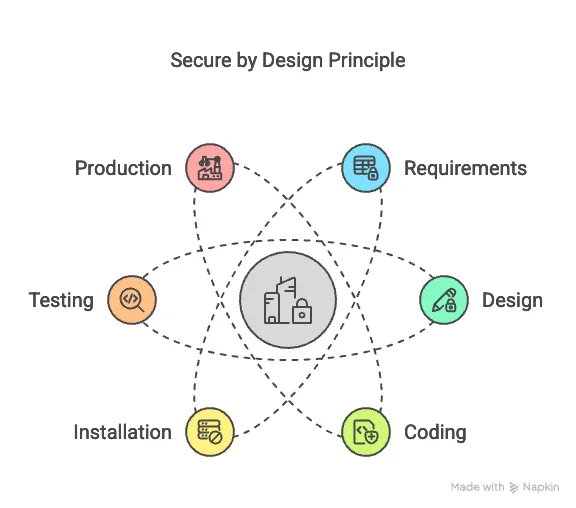
- Secure by Design Principle: Security should not be an afterthought or something "bolted on" at the end of the process. It must be integrated from the start, in the design phase, and be pervasive throughout the entire lifecycle (requirements, design, coding, installation, testing, and production). It’s compared to designing a building in an earthquake-prone area, where earthquake resistance is incorporated from the beginning, not after construction. Ideally, the system should be secure "out of the box."
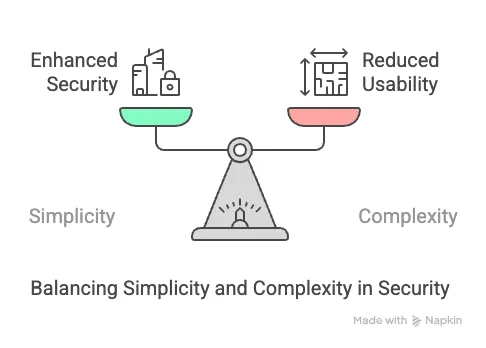
- K.I.S.S. Principle (Keep It Simple, Stupid): This principle warns against making things more complicated than necessary. Complexity is the enemy of security. An overly complex system can be easier for attackers and harder for legitimate users. If doing the right thing is harder than doing the wrong thing, people are likely to choose the wrong thing. An example is overly complex password rules that lead users to write down their passwords or reuse the same one across multiple systems. Complexity should be sufficient to keep attackers out but not so much that it hinders legitimate users. The challenge is balancing this principle with defense in depth.
I leave the one I shouldn't do to review the video myself here(also for you to check out and don't rely on my notes only here
Subscribe to my blog
